eBPF Unveiled: A Beginner’s Guide
In the ever-evolving landscape of software and systems programming, eBPF, or Extended Berkeley Packet Filter, has emerged as a groundbreaking technology that’s changing the rules of the game. It’s a name you might have heard whispered in developer circles, and for good reason. eBPF has brought about a revolution in the world of kernel programming, offering a level of flexibility, safety, and accessibility that was previously unimaginable.
The kernel, often referred to as the heart of an operating system, has long been a realm reserved for experts with a deep understanding of the inner workings of the system. The very thought of extending or modifying kernel behavior was enough to send shivers down the spines of even seasoned programmers. However, eBPF has transformed this once-daunting landscape into a fertile ground for innovation and experimentation, welcoming developers of all levels to the fold.
But what exactly is eBPF, and why is it generating so much excitement? To put it simply, eBPF is a technology that allows you to safely run custom programs inside the Linux kernel, offering a unique blend of flexibility, performance, and security. It’s not just a game-changer; it’s a game-opener.
In this journey into the realm of eBPF, we will unravel the mysteries behind this technology, understand how it works, and explore the vast possibilities it opens up for developers. Whether you’re a seasoned kernel programmer or someone taking their first steps into the world of systems development, eBPF promises a fascinating adventure that empowers you to reshape the way software interacts with the kernel. So, fasten your seatbelts and prepare to embark on an exhilarating exploration of eBPF, where we’ll demystify this innovation and discover how it’s revolutionizing the very core of our operating systems.
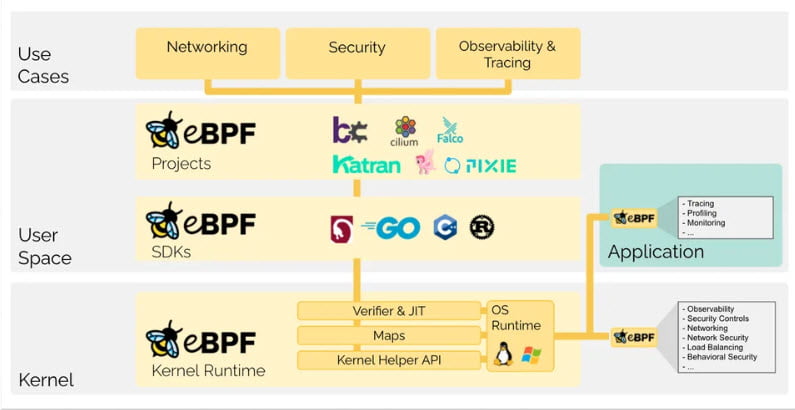
1. What is eBPF?
eBPF, which stands for Extended Berkeley Packet Filter, is a revolutionary technology that allows for programmability and extensibility within the Linux kernel. Originally derived from the traditional Berkeley Packet Filter (BPF) used for network packet filtering, eBPF extends its capabilities to a much broader range of applications beyond networking.
Key characteristics of eBPF include:
- Programmability: eBPF allows developers to write and load small programs (eBPF programs) into the kernel, which can be executed in response to various events, such as system calls, network packets, or tracepoints. This programmability enables a wide range of custom actions within the kernel.
- Safety: eBPF programs are designed to be safe and are executed in a restricted environment. They cannot crash the kernel or compromise system stability, which makes eBPF a secure technology for extending kernel functionality.
- Performance: eBPF programs are highly efficient and execute quickly. This is essential for tasks like packet processing, where low latency is critical.
- Observability: eBPF provides powerful tools for system observability, allowing developers to trace and monitor various aspects of the system, such as network traffic, disk I/O, and system calls. This is invaluable for troubleshooting, debugging, and performance analysis.
- Dynamic Updates: eBPF programs can be loaded into the kernel and updated at runtime without requiring a system reboot. This dynamic nature is particularly useful for real-time monitoring and security applications.
eBPF is versatile and can be used for a wide range of purposes, including:
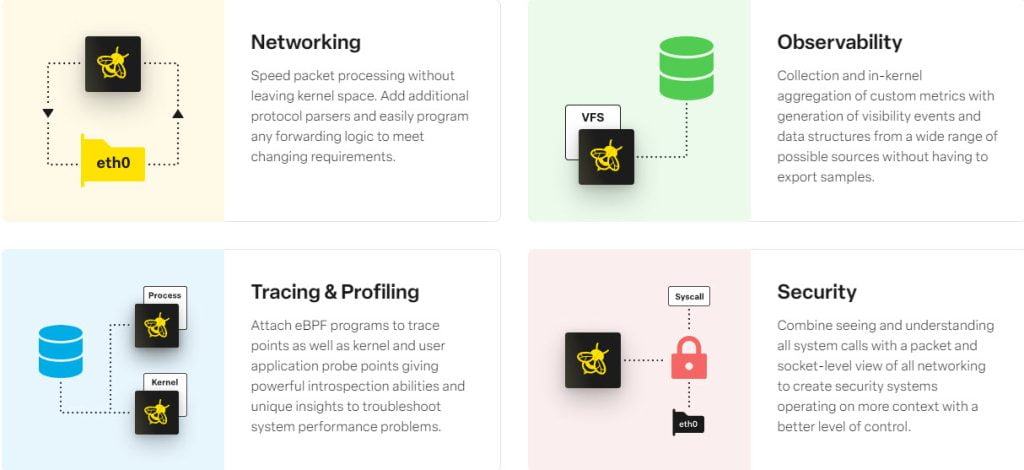
- Networking: eBPF is used for custom packet filtering, network traffic analysis, and network function virtualization.
- Security: It plays a significant role in enhancing security by allowing the implementation of custom security modules, intrusion detection systems, and monitoring of system activities.
- Observability: eBPF is a vital tool for observability, enabling system administrators and developers to gain insights into system behavior, performance bottlenecks, and debugging.
- Tracing: It enables the tracing of system calls, kernel functions, and user-space applications, providing a deep understanding of system interactions.
- Load Balancing: eBPF can be used for intelligent load balancing, traffic shaping, and network traffic management.
- Custom Protocols: It can be used to create custom protocols or extend existing ones, making it useful in both networking and data processing.
eBPF has gained popularity in the Linux ecosystem and is increasingly being adopted by the open-source community. It continues to evolve, with new features and use cases emerging regularly. As a result, eBPF is becoming an essential technology for enhancing and extending the capabilities of the Linux kernel, making it more flexible and adaptable to various applications and system requirements.
2. Why Program the Kernel?
Programming the kernel, the core of an operating system, is a task typically reserved for experts and system-level developers. But why would one want to venture into kernel programming? Here are some compelling reasons:
| Reason to Program the Kernel | Description |
|---|---|
| Optimization | Fine-tune the OS for performance, reduce latency, and enhance system responsiveness. |
| Hardware Interaction | Develop device drivers and kernel modules to communicate with specialized hardware components. |
| Security | Implement robust security mechanisms, access controls, and defenses against vulnerabilities. |
| Virtualization | Create or modify hypervisors, control virtual machine management, and enhance virtualization performance. |
| Specialized Software | Build software requiring low-level integration or system manipulation, such as real-time systems or custom file systems. |
| Innovative Features | Introduce new capabilities and functionalities to the OS not available in user-level applications. |
| Troubleshooting | Create custom debugging tools and diagnose and fix system issues at a low level. |
| Research and Education | Use kernel programming for academic research and educational purposes to understand OS internals. |
| IoT and Embedded Systems | Tailor OS for resource-constrained devices and enable efficient communication with sensors and actuators in IoT and embedded systems. |
| Customization | Customize the OS to meet specific application, industry, or hardware platform requirements. |
| Open Source Contribution | Contribute to open-source operating systems like Linux and collaborate with developers worldwide. |
| Security Research | Analyze vulnerabilities, develop security tools, and conduct research related to kernel-level security. |
Each of these reasons offers distinct advantages and opportunities for developers and organizations but requires a deep understanding of kernel-level programming and associated challenges.
3. How Does eBPF Work?
eBPF (Extended Berkeley Packet Filter) works by allowing developers to write and load small programs (eBPF programs) into the Linux kernel. These programs can be executed in response to specific events, such as system calls, network packets, or tracepoints. To understand how eBPF works, let’s break down the steps involved:
- Writing eBPF Programs:
- Developers write eBPF programs using a C-like domain-specific language specifically designed for eBPF. These programs are typically small and designed for a specific purpose, such as packet filtering, tracing, or event handling.
- eBPF programs are often structured as functions and include variables, loops, and logic for processing data and making decisions.
- Compiling eBPF Programs:
- Once an eBPF program is written, it needs to be compiled into a format that can be loaded into the kernel. LLVM (Low-Level Virtual Machine) is commonly used for this purpose.
- The eBPF compiler generates bytecode, which is a low-level representation of the program.
- Loading eBPF Programs into the Kernel:
- The compiled eBPF program is loaded into the Linux kernel using a loader. The most common loader is the
bpftoolcommand-line tool, although some higher-level frameworks and libraries provide more user-friendly interfaces. - Loading an eBPF program into the kernel involves the following steps: a. Verification: The loader performs verification to ensure that the eBPF program adheres to safety and security constraints. It checks for potential issues that could lead to crashes or vulnerabilities. b. BPF Maps: If the eBPF program needs to interact with data or share information with user space, it can use BPF maps. Maps are data structures that allow eBPF programs to store and retrieve information. These maps are created and initialized when loading the program. c. Attach Points: eBPF programs are attached to specific attach points, such as network interfaces, system calls, or tracepoints. These attach points determine when the eBPF program will be executed. d. Program Loading: Once verification, map creation, and attach point configuration are complete, the eBPF program is loaded into the kernel.
- The compiled eBPF program is loaded into the Linux kernel using a loader. The most common loader is the
- eBPF Program Execution:
- When an event that matches the attach point occurs, the associated eBPF program is executed. For example, if the eBPF program is attached to a network interface, it might be executed for each incoming packet.
- During execution, the eBPF program can perform various tasks, including filtering, tracing, collecting data, and making decisions.
- Data Exchange with User Space:
- eBPF programs can exchange data with user space through BPF maps. User space applications can read from or write to these maps to communicate with eBPF programs.
- This data exchange enables real-time monitoring, logging, and data analysis by user space applications.
- Dynamic Updates:
- One of the key advantages of eBPF is its ability to support dynamic updates. Developers can load new versions of eBPF programs or modify existing programs without rebooting the system.
- Dynamic updates are particularly valuable for real-time monitoring, security, and performance tuning.
- Error Handling and Debugging:
- eBPF programs can be monitored for errors, such as runtime issues or excessive resource consumption. Debugging tools and frameworks, such as
bpfccandlibbpf, help developers diagnose and troubleshoot eBPF programs.
- eBPF programs can be monitored for errors, such as runtime issues or excessive resource consumption. Debugging tools and frameworks, such as
By following these steps, eBPF programs become an integral part of the Linux kernel, allowing for real-time, safe, and efficient customization of kernel behavior. This flexibility and programmability are leveraged in a variety of use cases, making eBPF a powerful technology for enhancing observability, security, and performance in Linux systems.
4. What’s possible with eBPF?
eBPF (Extended Berkeley Packet Filter) offers a wide range of possibilities and use cases due to its programmability and extensibility within the Linux kernel.
Here are some of the things that are possible with eBPF:
| eBPF Use Cases | Description |
|---|---|
| Network Packet Filtering | Fine-grained packet filtering and manipulation at the kernel level for firewalling, traffic shaping, and security policies. |
| Real-time Network Monitoring | Capture, analyze, and visualize network traffic in real time for network performance monitoring and security. |
| Custom Load Balancers | Creation of custom load balancers to distribute network traffic efficiently based on various criteria. |
| Custom Protocols | Development of custom networking protocols for specialized applications, industries, or custom communication needs. |
| Security and Intrusion Detection | Real-time monitoring of system calls, network activity, and user behavior for security threat detection and response. |
| Performance Tuning | Performance monitoring and optimization of kernel functions and system components for high-performance applications. |
| File System Tracing | Tracing of file system activity for debugging and auditing purposes, providing insights into file access and modification. |
| Dynamic Tracing and Profiling | Dynamic tracing and profiling of applications and the kernel for in-depth analysis of performance bottlenecks and system behavior. |
| Kernel Function Monitoring | Tracing and analysis of kernel function calls and parameters, offering detailed insight into kernel internals. |
| User-space Application Tracing | Tracing of user-space applications, monitoring system calls and application behavior for debugging and performance analysis. |
| Distributed Systems Observability | Monitoring and tracing of interactions between services and microservices in distributed systems for application performance and dependency analysis. |
| Dynamic Security Modules | Creation of custom security modules that enforce access controls, detect security breaches, and protect the system from vulnerabilities. |
| Custom Probes for Tracing | Creation of custom tracepoints to instrument application behavior for performance analysis and monitoring. |
| IoT and Embedded Systems | Optimization of resource usage, sensor monitoring, and security for IoT and embedded systems. |
| Dynamic Updates | Ability to update or replace eBPF programs at runtime without system reboots, adapting to changing requirements and evolving threats. |
| Custom Analytics and Data Collection | Custom data collection, analytics, and data processing for telemetry, data aggregation, and real-time analytics. |
| Performance Analysis of Containers and Orchestration Platforms | Insights into the performance of containerized applications and orchestration platforms for resource allocation and scaling optimization. |
| Resource Usage Tracking | Tracking of resource usage (CPU, memory, disk I/O) for individual processes or containers to aid in resource management and optimization. |
Each of these use cases demonstrates how eBPF’s programmability and extensibility within the Linux kernel can be leveraged to address a wide range of system-level challenges and opportunities.
5. Wrapping Up
In conclusion, eBPF (Extended Berkeley Packet Filter) stands as a transformative technology that has redefined the way we interact with the Linux kernel. Its programmability, efficiency, and safety have unleashed a world of possibilities, empowering developers and system administrators to tackle a diverse array of challenges, from network management and security to observability, performance optimization, and custom protocol development.
The ability to filter, trace, and analyze network traffic in real time, coupled with the dynamic nature of eBPF that allows for on-the-fly updates, has elevated network monitoring and security to new heights. It has given rise to custom load balancers and protocols, enhancing performance and adaptability in the ever-changing landscape of applications.
In the realm of security and intrusion detection, eBPF enables real-time vigilance, responding swiftly to emerging threats and vulnerabilities. It grants us the power to scrutinize kernel function calls, user-space applications, and distributed systems, unveiling valuable insights into system behavior and performance bottlenecks.
eBPF’s reach extends to file system tracing, dynamic profiling, and the monitoring of user-space applications, making it an invaluable tool for debugging and performance optimization. It opens doors to IoT and embedded systems, where resource optimization and security are paramount, while its support for containers and orchestration platforms ensures high-performance scalability in modern cloud environments.
The capacity to create dynamic security modules and custom tracepoints allows for tailored access control and in-depth performance analysis, while eBPF adapts to the ever-evolving landscape with its ability to update and replace programs without system reboots.
In a data-driven world, eBPF is the gateway to custom analytics, data collection, and real-time data processing, offering solutions that respond to the rapid pace of data generation and consumption.