Starting with DevSecOps Cheatsheet
1. Introduction
The primary goal of DevSecOps is to foster a culture of shared responsibility, collaboration, and continuous improvement. By incorporating security from the very beginning and throughout the software development lifecycle, organizations can proactively address vulnerabilities and ensure the resilience of their applications and systems.
DevSecOps, short for Development, Security, and Operations, is an innovative approach to software development that emphasizes integrating security practices and principles into every phase of the software development lifecycle. It represents a fundamental shift in how organizations traditionally approach software development by prioritizing security from the very beginning and integrating it seamlessly into the development process.DevSecOps aims to break down the silos between development, security, and operations teams, fostering collaboration and shared responsibility throughout the software development process.
By adopting this approach, organizations can address security concerns proactively, minimize vulnerabilities, and deliver more secure and resilient software solutions. The benefits of adopting a DevSecOps approach are numerous. It allows organizations to respond more effectively to the constantly evolving threat landscape, reduce the time required to detect and mitigate security issues, and ultimately deliver more secure and reliable software products. Moreover, by integrating security into the development process, organizations can achieve better alignment between security and business objectives, leading to enhanced customer trust and competitive advantage.
1.1 Understanding DevSecOps
DevSecOps is an approach to software development that combines development (Dev), security (Sec), and operations (Ops) practices into a unified and collaborative process. It aims to integrate security measures and considerations into every stage of the software development lifecycle, from design and coding to testing, deployment, and operations. Traditionally, software development processes have often treated security as a separate and isolated concern, addressed late in the development cycle or as an afterthought. This approach can lead to vulnerabilities and security issues being discovered too late, causing delays, increased costs, and potential breaches.
DevSecOps, on the other hand, advocates for security to be an inherent part of the development process from the beginning. It promotes a shift-left mentality, where security practices are applied early on and continuously throughout development. By incorporating security practices into the DevOps workflow, organizations can proactively identify and address security risks, reduce vulnerabilities, and ensure that software is secure by design.
DevSecOps also embraces automation and tooling to streamline security practices, enabling developers to easily incorporate security controls into their workflows. By providing developers with the necessary tools and resources to build secure code, DevSecOps empowers them to take ownership of security and ensures that security measures are implemented consistently and efficiently across the software development lifecycle.
1.2 Essential Themes in DevSecOps
The key themes of DevSecOps can be summarized as follows:
| Key Principles of DevSecOps | Description |
|---|---|
| Collaboration and Shared Responsibility | DevSecOps emphasizes collaboration and shared responsibility among development, security, and operations teams. |
| Shift-Left Security | DevSecOps promotes the concept of “shifting left” security, which means integrating security practices and considerations early in the software development lifecycle. |
| Automation and Tooling | DevSecOps relies on automation tools to streamline security practices and reduce manual efforts. |
| Continuous Security Testing | DevSecOps advocates for continuous security testing throughout the development lifecycle. |
| Compliance and Governance | DevSecOps promotes integrating security controls and compliance requirements into the development process. |
| Risk Management | DevSecOps emphasizes a risk-based approach to security. |
| Continuous Monitoring and Feedback | DevSecOps advocates for continuous monitoring of the software in production. |
| Education and Awareness | DevSecOps recognizes the importance of education and awareness among developers, security professionals, and other stakeholders. |
By embracing these key themes, organizations can create a culture of security and collaboration, enabling them to build and deploy software that is inherently secure, resilient, and aligned with business objectives.
1.2.1 Avoid These Three Mistakes in Enterprise Organizations
Here are three common mistakes to avoid in enterprise organizations when implementing DevSecOps:
- Lack of Collaboration and Communication: One of the biggest mistakes in DevSecOps implementation is failing to foster collaboration and communication between development, security, and operations teams. It’s crucial to break down silos and establish regular communication channels to ensure that security considerations are integrated into every stage of the software development lifecycle.
- Inadequate Security Training and Awareness: Neglecting to provide sufficient security training and awareness programs to developers and other stakeholders can undermine the effectiveness of DevSecOps. It’s essential to educate and empower team members with the necessary knowledge and skills to identify and address security issues. A lack of security awareness can lead to the introduction of vulnerabilities and weak security practices in software development processes.
- Insufficient Automation and Tooling: Another mistake is not investing in automation and appropriate tooling to support the DevSecOps workflow. Automation plays a crucial role in streamlining security practices, such as continuous integration, continuous deployment, and automated security testing. Without adequate automation and tooling, organizations may struggle to effectively integrate security into their development pipelines and detect vulnerabilities on time.
These three mistakes highlight the importance of collaboration, training, awareness, and automation in successful DevSecOps implementation within enterprise organizations. By avoiding these pitfalls, organizations can enhance their security posture and ensure the successful integration of security into their software development practices.
1.3 Unveiling the “Phoenix” Initiative
The three ways of security in DevSecOps talk about the Phoenix project. The Phoenix Project is a book written by Gene Kim, Kevin Behr, and George Spafford that explores the challenges and solutions in transforming an organization’s IT operations. While the book doesn’t specifically address security in DevSecOps, we can relate the three ways of security in DevSecOps to the principles discussed in The Phoenix Project. Here’s an interpretation:
- Shift-Left Security and Alignment of Security Goals: The first way of security in DevSecOps aligns with the principle of shifting security to the left. Similarly, in The Phoenix Project, the first way focuses on creating an understanding and alignment of goals across different teams. In the context of security, this means involving security professionals early in the development process and ensuring that security objectives and requirements are communicated to all stakeholders.
- Automated Security Testing and Amplification of Feedback: The second way of security in DevSecOps aligns with the concept of automated security testing. In The Phoenix Project, the second way emphasizes the need for feedback loops and amplifies feedback quickly and effectively. Similarly, in DevSecOps, organizations implement automated security testing tools and processes to provide continuous feedback on the security of their software. This helps identify vulnerabilities early, enabling faster remediation and reducing security risks.
- Continuous Monitoring and Response, and Creating a Culture of Learning: The third way of security in DevSecOps relates to continuous monitoring and response. In The Phoenix Project, the third way focuses on creating a culture of learning and improvement. In the context of security, this means establishing continuous monitoring mechanisms, such as real-time security monitoring and incident response processes, to identify and respond to security incidents promptly. It also involves fostering a culture of learning from security events, conducting post-incident reviews, and implementing improvements to prevent similar incidents in the future.
By drawing parallels between the three ways of security in DevSecOps and the principles discussed in The Phoenix Project, organizations can understand the importance of aligning goals, leveraging automation and feedback loops, and fostering a culture of learning and improvement in their security practices.
1.4 Advantages and Disadvantages of DevSecOps
1.4.1 Advantages
DevSecOps offers several advantages for organizations:
- Improved security posture: DevSecOps integrates security practices throughout the software development lifecycle, ensuring that security considerations are addressed early on and continuously. By embedding security into every stage of development, organizations can enhance their overall security posture and reduce the risk of vulnerabilities and security breaches.
- Faster time to market: DevSecOps promotes automation, continuous integration, and continuous delivery (CI/CD) practices. This automation streamlines the development and deployment processes, allowing organizations to release software faster and more frequently. By integrating security into these automated processes, security measures can be implemented without significantly slowing down development cycles.
- Early detection and mitigation of vulnerabilities: DevSecOps incorporates security testing and scanning tools into the development pipeline, enabling the early detection and mitigation of vulnerabilities. Automated security testing helps identify security weaknesses, such as code flaws or misconfigurations, and allows developers to address them promptly before they become more complex and expensive to fix.
- Increased collaboration and communication: DevSecOps fosters collaboration between development, operations, and security teams. This collaboration improves communication, knowledge sharing, and mutual understanding of each team’s requirements and concerns. By working together, teams can align their efforts toward building secure and reliable software.
- Continuous compliance and auditing: Compliance with regulatory standards and industry best practices is essential for many organizations. DevSecOps enables continuous compliance by integrating compliance checks and audits into the development process. This approach ensures that security controls and requirements are met consistently, reducing the effort and potential disruptions associated with compliance assessments.
- Risk reduction and mitigation: By addressing security early in the development process, DevSecOps helps mitigate risks associated with software vulnerabilities and security breaches. Proactive identification and mitigation of security issues minimize the likelihood of successful attacks and potential damage to the organization’s reputation, financial stability, and customer trust.
- Agile and adaptive security: DevSecOps promotes an agile and adaptive security mindset. Security measures can be continuously evaluated, adjusted, and improved based on emerging threats, evolving security standards, and changing business requirements. This allows organizations to stay resilient and respond effectively to new security challenges.
1.4.2 Disadvantages
While DevSecOps brings numerous benefits, there are also some potential disadvantages or challenges associated with its implementation. Here are a few disadvantages of DevSecOps:
- Initial investment and learning curve: Adopting DevSecOps practices may require an initial investment in terms of resources, tools, and training. Organizations need to allocate time and resources to train their teams on security practices, implement new tools and technologies, and establish new processes. This initial learning curve and investment can be a challenge for some organizations, especially those with limited resources or resistance to change.
- Integration complexities: Integrating security practices into the development process can introduce complexities. Organizations may face challenges in integrating security tools and practices seamlessly into their existing development workflows. Compatibility issues, configuration challenges, and the need to align with different development environments and technologies can create additional overhead and slow down the development process.
- Balancing speed and security: DevSecOps aims to enable faster software delivery while ensuring security. However, there can be a potential tension between speed and security requirements. Striking the right balance between rapid development cycles and robust security measures can be challenging. Organizations need to find ways to prioritize security without causing significant delays or compromising the agility and speed of software delivery.
- Skill gaps and expertise: Implementing DevSecOps requires skilled personnel who possess expertise in both development and security domains. Finding individuals with a strong understanding of both areas can be challenging, and organizations may need to invest in training or hiring specialized talent. Bridging the skill gaps between development and security teams can take time and effort.
- Cultural and organizational challenges: DevSecOps requires a cultural shift and a collaborative mindset across different teams, including developers, operations, and security professionals. Overcoming organizational silos, fostering effective communication, and promoting a shared responsibility for security can be challenging. Resistance to change and the need to align different teams with varying priorities and perspectives may slow down the adoption of DevSecOps practices.
- Continuous monitoring and maintenance: DevSecOps promotes continuous monitoring and maintenance of security measures throughout the software development lifecycle. This ongoing effort requires dedicated resources and attention to ensure that security controls remain effective, vulnerabilities are promptly addressed, and compliance is maintained. Organizations need to allocate resources and establish processes for continuous monitoring, maintenance, and updating of security practices.
2. DevSecOps Journey: A Beginner’s Guide
Here’s an example of how you can get started with DevSecOps by incorporating security into a “Hello, World!” application:
- Set Up Version Control: Start by setting up a version control system like Git to manage your codebase. Initialize a new repository and create a simple “Hello, World!” application.
- Integrate Security Code Analysis: Choose a security code analysis tool such as SonarQube or Snyk. Configure the tool to scan your code for potential security vulnerabilities, coding best practices, and other issues. This can be done as part of your CI/CD pipeline or during the development process.
- Implement Automated Testing: Create automated security tests to validate the security of your application. This can include testing for common vulnerabilities such as injection attacks, cross-site scripting (XSS), or insecure direct object references (IDOR). Integrate these security tests into your CI/CD pipeline to run them automatically with each code commit or deployment.
- Containerize Your Application: Containerization provides an additional layer of security and portability. Docker is a popular choice for containerization. Containerize your “Hello, World!” application by creating a Dockerfile and packaging your application into a Docker container.
- Container Image Scanning: Use container image scanning tools like Clair or Anchore to scan your Docker image for known vulnerabilities. This helps identify and address any security issues within the container image before deployment.
- Continuous Monitoring and Logging: Implement continuous monitoring and logging practices to gain visibility into the runtime behavior of your application. Utilize tools like Prometheus, ELK stack (Elasticsearch, Logstash, and Kibana), or Splunk to collect and analyze logs and metrics. Set up alerts to detect any suspicious activities or security-related events.
- Security Incident Response: Establish a security incident response process to handle any security incidents or vulnerabilities discovered. Define roles and responsibilities, establish communication channels, and document procedures for identifying, mitigating, and resolving security incidents.
- Education and Awareness: Promote security education and awareness among your development and operations teams. Conduct security training sessions to educate team members on secure coding practices, common vulnerabilities, and security best practices. Encourage a security-first mindset and foster a culture of continuous learning and improvement.
Remember, this is a basic “Hello, World!” example, but the principles can be applied to more complex applications. The key is to integrate security throughout the entire software development lifecycle, automate security practices, and continuously monitor and improve the security of your applications.
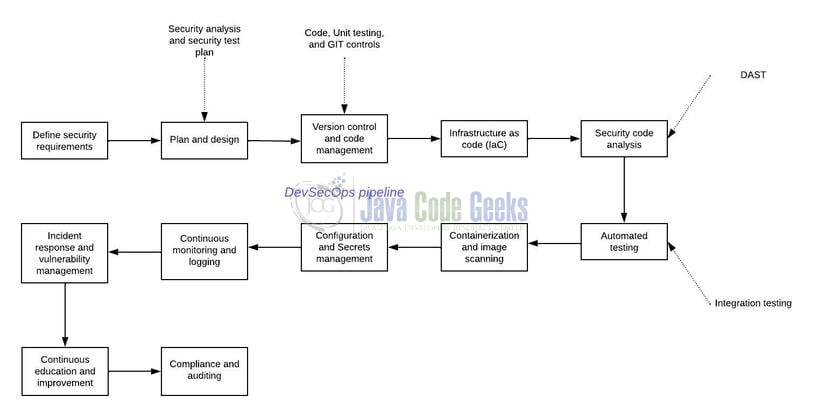
2.1 DevSecOps Pipeline: Building the Bridge
Creating a DevSecOps pipeline involves integrating security practices and tools into your software development lifecycle. Here are the key steps to create a DevSecOps pipeline:
- Define Security Requirements: Identify the security requirements and objectives specific to your application or organization. This could include compliance regulations, security standards, or industry best practices.
- Plan and Design: Plan and design your DevSecOps pipeline. Consider the stages of your pipeline, such as code development, testing, deployment, and monitoring. Determine how security practices and tools will be integrated into each stage.
- Version Control and Code Management: Use a version control system like Git to manage your codebase. Implement branching strategies and policies to ensure code integrity and traceability.
- Infrastructure as Code (IaC): Apply Infrastructure as Code principles to define and manage your infrastructure. Use tools like Terraform or AWS CloudFormation to automate the provisioning and configuration of infrastructure resources, ensuring consistency and security.
- Security Code Analysis: Integrate security code analysis tools into your pipeline. Tools like SonarQube or Snyk can scan your code for potential security vulnerabilities, coding best practices, and other issues. Set up automated scans triggered by code commits or pull requests.
- Automated Testing: Implement automated security testing to validate the security of your application. This can include static application security testing (SAST), dynamic application security testing (DAST), or software composition analysis (SCA) tools. Include security tests as part of your continuous integration and continuous deployment (CI/CD) pipeline.
- Containerization and Image Scanning: Containerize your application using tools like Docker or Kubernetes. Scan your container images for known vulnerabilities using tools like Clair or Anchore before deployment. Automate this process as part of your CI/CD pipeline.
- Configuration and Secrets Management: Use configuration management tools like Ansible or Chef to manage and secure your application configurations. Implement secrets management tools to securely store and manage sensitive information such as passwords and API keys.
- Continuous Monitoring and Logging: Implement continuous monitoring practices to gain real-time visibility into the security of your application. Utilize tools like Prometheus, ELK stack (Elasticsearch, Logstash, and Kibana), or Splunk to collect and analyze logs and metrics. Set up alerts for security-related events.
- Incident Response and Vulnerability Management: Establish a security incident response process to handle security incidents or vulnerabilities discovered. Define roles, responsibilities, and communication channels. Implement vulnerability management practices to identify, prioritize, and remediate vulnerabilities.
- Continuous Education and Improvement: Promote security education and awareness among your teams. Provide training on secure coding practices, common vulnerabilities, and security best practices. Foster a culture of continuous learning and improvement by conducting security-related retrospectives and implementing lessons learned.
- Compliance and Auditing: Ensure your DevSecOps pipeline complies with relevant regulations and standards. Conduct regular audits to assess the effectiveness of your security practices and address any compliance gaps.
Remember that each organization’s DevSecOps pipeline will vary based on specific requirements and technology stack. It’s important to continuously assess and refine your pipeline to adapt to evolving security threats and best practices.
2.2 Security Tools and Technologies: Making Informed Choices
When choosing security tools and technologies for DevSecOps, it’s important to consider your specific requirements, the nature of your applications, and the overall goals of your DevSecOps initiative. Here are some factors to consider when selecting security tools and technologies:
- Comprehensive Security Coverage: Look for tools that offer a wide range of security capabilities to cover various aspects of application security, such as code analysis, vulnerability scanning, threat detection, access management, and compliance.
- Integration with DevOps Toolchain: Ensure that the security tools can seamlessly integrate with your existing DevOps toolchain, including version control systems, CI/CD platforms, and deployment automation tools. The integration enables smooth collaboration and automation across the entire development and deployment lifecycle.
- Automation and Continuous Monitoring: Choose tools that support automation and continuous monitoring to provide real-time insights into the security posture of your applications. Automated security testing, vulnerability scanning, and log analysis help identify and address security issues at an early stage.
- Scalability and Performance: Consider the scalability and performance requirements of your applications and evaluate whether the security tools can handle the expected workload without causing performance bottlenecks or delays in the development and deployment processes.
- Open Source or Commercial: Decide whether to use open-source security tools or opt for commercial solutions. Open-source tools often offer flexibility and community support, while commercial tools may provide additional features, support, and dedicated customer service.
- Vendor Reputation and Support: Research the reputation and track record of the tool vendors. Look for vendors with a good reputation, established customer base, and positive reviews. Also, consider the level of support they provide, including documentation, training, and customer support channels.
- Compliance and Regulatory Requirements: If your applications need to comply with specific regulations or standards, ensure that the security tools align with those requirements. Look for tools that provide compliance checks, reporting, and auditing capabilities to help you meet the necessary security standards.
- User-Friendly Interface and Usability: Evaluate the user interface and usability of the security tools. A user-friendly interface simplifies configuration, monitoring, and analysis, making it easier for your development and security teams to collaborate effectively.
- Cost Considerations: Consider the costs associated with the security tools, including licensing fees, maintenance, and ongoing support. Evaluate the value provided by the tools about their cost and ensure that they fit within your budget constraints.
- Community and Ecosystem: Assess the size and activity of the tool’s user community and ecosystem. A vibrant community can provide valuable resources, plugins, and integrations that enhance the functionality and usefulness of security tools.
Remember to prioritize the tools that align with your specific security goals and requirements. It’s also recommended to conduct proof-of-concept evaluations or trials to assess the suitability of the tools within your organization’s environment before making a final decision.
2.2.1 Different code scanning and security tools
- SAST Tools (Static Application Security Testing): These tools, such as SonarQube and Veracode, analyze the source code or compiled code of an application to identify potential security vulnerabilities and coding errors.
- DAST Tools (Dynamic Application Security Testing): OWASP ZAP and Burp Suite are examples of DAST tools. They evaluate the security of running applications by sending various requests and analyzing the responses, helping to identify vulnerabilities that may arise during runtime.
- IAST Tools (Interactive Application Security Testing): IAST tools like Contrast Security and Synopsys provide real-time monitoring of applications during runtime. By instrumenting the code, they detect vulnerabilities and provide insights into the specific components causing the issues.
- SCA Tools (Software Composition Analysis): SCA tools like Black Duck and WhiteSource examine the open-source components used in an application’s codebase. They identify any known vulnerabilities or license compliance issues associated with the third-party libraries and dependencies.
2.2.2 Difference code scanning and security tools
| Tool | Advantages | Disadvantages |
|---|---|---|
| Static Application Security Testing |
|
|
| Dynamic Application Security Testing |
|
|
| Interactive Application Security Testing |
|
|
| Software Composition Analysis |
|
|
3. Core Practices in DevSecOps
DevSecOps practices refer to the integration of security practices and principles into the DevOps approach. It aims to ensure that security is treated as an integral part of the software development and deployment process, rather than an afterthought. By incorporating security early on and throughout the development lifecycle, DevSecOps practices help organizations build secure and resilient systems. Here are some key DevSecOps practices:
| Key Practices in DevSecOps | Description |
|---|---|
| Shift-Left Security | DevSecOps emphasizes shifting security practices and considerations to the left, meaning security is incorporated early in the development process. This involves involving security professionals from the beginning, conducting security reviews, threat modeling, and integrating security tools into the development environment. |
| Security Automation | Automation plays a crucial role in DevSecOps practices. By automating security processes, such as code analysis, vulnerability scanning, and compliance checks, organizations can identify security issues early and address them efficiently. Automation also helps ensure consistency and repeatability in security practices. |
| Continuous Security Testing | Continuous security testing is a core practice in DevSecOps. It involves integrating security testing, such as static application security testing (SAST), dynamic application security testing (DAST), and software composition analysis (SCA), into the CI/CD pipeline. This enables security vulnerabilities and weaknesses to be detected and addressed rapidly as part of the development and deployment process. |
| Infrastructure as Code (IaC) Security | In DevSecOps, security is extended beyond application code to include infrastructure. Infrastructure as Code (IaC) practices allow organizations to define and manage their infrastructure through code. By incorporating security controls and best practices into IaC templates and scripts, organizations can ensure consistent and secure infrastructure provisioning. |
| Secure Configuration Management | Secure configuration management involves implementing secure configurations for all components of the application stack, including servers, databases, and network devices. By following security configuration guidelines and regularly auditing and updating configurations, organizations can mitigate security risks. |
| Continuous Monitoring and Incident Response | Continuous monitoring is crucial to identify and respond to security incidents promptly. DevSecOps encourages the implementation of real-time security monitoring, log analysis, and threat intelligence to detect and respond to security events. Incident response plans and processes should be established to handle security incidents effectively. |
| Security Awareness and Education | Building a security-conscious culture is vital in DevSecOps. Organizations should invest in security awareness and education programs to train developers, operations teams, and other stakeholders on secure coding practices, security threats, and best practices. Continuous learning and knowledge sharing help foster a security-first mindset. |
| Compliance and Governance | DevSecOps practices should align with relevant regulations, industry standards, and compliance requirements. Organizations need to integrate compliance checks, reporting, and auditing capabilities into their processes to ensure adherence to security standards and regulations. |
| Collaboration and Communication | Effective collaboration and communication between development, operations, and security teams are essential in DevSecOps. Teams should work together to share information, identify risks, and implement security controls. Collaboration tools and practices should be adopted to facilitate seamless communication and cooperation. |
By embracing these DevSecOps practices, organizations can build secure, scalable, and resilient systems while maintaining the speed and agility provided by the DevOps approach.
3.1 DevSecOps with Additional Practices
In addition to the core practices of integrating security into the software development process, several additional practices can enhance the effectiveness of DevSecOps:
| Security Practices | Description |
|---|---|
| Threat modeling | Conducting threat modeling helps identify potential security threats and vulnerabilities in the system early on. This practice involves analyzing the system architecture, identifying potential attack vectors, and prioritizing security measures based on the identified risks. Threat modeling helps in designing and implementing appropriate security controls. |
| Secure coding guidelines | Establishing and enforcing secure coding guidelines is crucial for building secure software. These guidelines provide developers with best practices for writing secure code, such as input validation, output encoding, and secure authentication mechanisms. Regular code reviews and automated code analysis tools can help ensure adherence to these guidelines. |
4. Different DevSecOps Tools
4.1 Configuration Management Tools
Configuration management is a vital aspect of modern software development and IT operations. It involves managing and controlling the configuration of software systems, infrastructure, and applications throughout their lifecycle. Configuration management tools play a critical role in automating and simplifying this process.
Configuration management tools enable organizations to standardize and automate the deployment, configuration, and maintenance of software and infrastructure components. These tools provide a centralized platform for managing configuration files, settings, and parameters across different environments, ensuring consistency and reliability.
One of the key benefits of configuration management tools is their ability to enforce desired states. They allow teams to define and maintain the desired configuration of systems and automatically apply any necessary changes to ensure the systems align with the desired state. This helps in reducing configuration drift, where systems deviate from their intended configuration over time.
These tools also facilitate infrastructure as code (IaC) practices, where infrastructure and configuration are defined and managed using code. By treating infrastructure as code, organizations can version control their configuration, track changes, and reproduce environments accurately.
Configuration management tools offer a range of features and capabilities, including declarative configuration languages, dependency management, automated provisioning, and orchestration. They integrate with various platforms, cloud providers, and operating systems, enabling organizations to manage complex and diverse environments seamlessly.
Some popular configuration management tools include Ansible, Puppet, and Chef. These tools provide robust solutions for automating configuration management tasks, enabling teams to scale their operations, improve efficiency, and reduce manual errors.
4.1.1 Ansible
Ansible is an open-source automation platform that simplifies the management and configuration of systems and applications. It uses a declarative language called YAML (YAML Ain’t Markup Language) to define the desired state of infrastructure and perform tasks across multiple machines. Here’s a sample code snippet that demonstrates the use of Ansible to install and configure a web server:
- name: Install and configure Apache web server
hosts: webserver
become: true
tasks:
- name: Install Apache package
apt:
name: apache2
state: present
- name: Enable Apache service
service:
name: apache2
enabled: true
state: started
- name: Copy custom index.html file
copy:
src: /path/to/index.html
dest: /var/www/html/index.html
owner: root
group: root
mode: 0644
4.1.2 Puppet
Puppet is a configuration management tool that automates the provisioning, configuration, and management of systems. It uses a declarative language called Puppet DSL to define the desired state of the infrastructure. Here’s a sample Puppet manifest that installs and configures a web server:
node 'webserver' {
package { 'apache2':
ensure => installed,
}
service { 'apache2':
ensure => running,
enable => true,
require => Package['apache2'],
}
file { '/var/www/html/index.html':
ensure => file,
source => '/path/to/index.html',
owner => 'root',
group => 'root',
mode => '0644',
require => Package['apache2'],
notify => Service['apache2'],
}
}
4.1.3 Chef
Chef is a powerful configuration management and automation tool that allows you to define infrastructure as code. It uses a domain-specific language (DSL) to describe the desired state of systems and automate the configuration process. Here’s a sample Chef recipe that installs and configures a web server:
package 'apache2' do action :install end service 'apache2' do action [:enable, :start] end cookbook_file '/var/www/html/index.html' do source 'index.html' owner 'root' group 'root' mode '0644' action :create notifies :restart, 'service[apache2]' end
4.2 Continuous Integration and Delivery Tools
Continuous Integration and Delivery (CI/CD) has become a crucial practice in modern software development, enabling teams to deliver high-quality software faster and more efficiently. CI/CD tools play a vital role in automating the build, testing, and deployment processes, ensuring smooth and reliable software delivery pipelines.
CI/CD tools facilitate the integration of code changes from multiple developers into a shared repository, where automated builds and tests are triggered. These tools enable teams to catch integration issues early, identify bugs, and ensure that the codebase remains stable. By continuously integrating code changes, developers can collaborate effectively and detect and resolve issues more efficiently.
Continuous Delivery (CD) takes CI a step further by automating the deployment process. CD tools enable organizations to package, deploy, and release software applications consistently across different environments. By automating the deployment process, teams can reduce manual errors, ensure consistency, and achieve faster time-to-market.
CI/CD tools offer a wide range of features to support the development and delivery lifecycle. They often provide capabilities such as code repository integration, build automation, automated testing, artifact management, and deployment orchestration. These tools integrate with popular version control systems like Git and support various programming languages and frameworks.
One of the key benefits of CI/CD tools is the ability to automate the entire software delivery pipeline, from source code management to production deployment. They provide visibility into the build and deployment process, allowing teams to track changes, monitor progress, and identify bottlenecks. With automated testing and quality checks, these tools help maintain code quality and ensure that only reliable and well-tested software is released.
4.2.1 Jenkins
Jenkins is an open-source automation server that enables continuous integration and continuous delivery (CI/CD) of software projects. It provides a wide range of plugins and integrations, allowing for easy customization and extensibility. Here’s an example of a Jenkins pipeline script that builds and deploys a web application:
pipeline {
agent any
stages {
stage('Build') {
steps {
sh 'npm install'
}
}
stage('Test') {
steps {
sh 'npm test'
}
}
stage('Deploy') {
steps {
sh 'npm run deploy'
}
}
}
}
4.2.2 GitLab CI/CD
GitLab CI/CD is a built-in continuous integration and continuous delivery platform provided by GitLab. It allows you to define CI/CD pipelines using a configuration file called .gitlab-ci.yml. Here’s an example .gitlab-ci.yml file that builds and deploys a web application:
stages:
- build
- test
- deploy
build:
stage: build
script:
- npm install
test:
stage: test
script:
- npm test
deploy:
stage: deploy
script:
- npm run deploy
4.2.3 CircleCI
CircleCI is a cloud-based CI/CD platform that automates the build, test, and deployment processes. It provides a simple and intuitive configuration file called config.yml to define the pipeline. Here’s an example config.yml file for building and deploying a web application:
version: 2.1
jobs:
build-and-deploy:
docker:
- image: node:latest
steps:
- checkout
- run:
name: Build
command: npm install
- run:
name: Test
command: npm test
- run:
name: Deploy
command: npm run deploy
4.3 Containerization and Orchestration Tools
Containerization and orchestration have become fundamental pillars of modern application deployment and management. Containerization tools enable organizations to package applications and their dependencies into lightweight, portable containers, while orchestration tools automate the deployment, scaling, and management of these containers. Together, they revolutionize software delivery, scalability, and resilience. Some popular containerization and orchestration tools include:
4.3.1 Docker
Docker is an open-source platform that allows you to automate the deployment and management of applications within lightweight, isolated containers. It provides a way to package applications and their dependencies into portable containers that can run consistently across different environments. Here’s an example of using Docker to run a web server:
docker run -d -p 80:80 nginx – This command pulls the Nginx image from the Docker registry and runs it in a container, mapping port 80 of the host to port 80 of the container. This allows the Nginx web server to be accessed on the host machine.
4.3.2 Kubernetes
Kubernetes is an open-source container orchestration platform that automates the deployment, scaling, and management of containerized applications. It provides a highly flexible and resilient architecture to run and manage containers across clusters of machines. Here’s an example of deploying an application on Kubernetes:
kubectl create deployment my-app --image=myapp:1.0 – This command creates a deployment called “my-app” using the container image “myapp:1.0”. Kubernetes will automatically schedule and manage the application pods based on the desired state defined in the deployment.
4.3.3 OpenShift
OpenShift is a container application platform that builds on top of Kubernetes. It provides an enterprise-ready, fully managed container platform with additional features and capabilities for application development, deployment, and scaling. Here’s an example of deploying an application on OpenShift:
oc new-app myapp:1.0 – This command creates a new application called “myapp” using the container image “myapp:1.0” and automatically sets up the necessary resources, such as deployment configurations, services, and routes, to run the application on OpenShift.
4.4 Security Information and Event Management (SEM) Tools
SIEM tools provide a centralized platform for collecting, analyzing, and correlating security event data from various sources, such as logs, network devices, applications, and endpoints. By aggregating and analyzing this data, SIEM tools enable organizations to detect and respond to security incidents in real time, as well as proactively identify potential threats.
The primary goal of SIEM tools is to provide comprehensive visibility into an organization’s security posture. They help security teams monitor and analyze logs and events from diverse sources, identify patterns, and generate actionable insights. SIEM tools use advanced correlation algorithms, anomaly detection, and threat intelligence feeds to identify potential security incidents, such as unauthorized access attempts, malware infections, or data breaches.
SIEM tools offer a wide range of features and capabilities. They provide real-time event monitoring, log management, and log analysis capabilities. They can automatically aggregate and normalize log data from different sources, making it easier to identify patterns and detect security events. SIEM tools also provide alerting and notification mechanisms to ensure that security teams can respond promptly to potential threats or incidents.
Another critical aspect of SIEM tools is their reporting and compliance capabilities. They help organizations meet regulatory requirements by providing pre-built reports and facilitating audit processes. SIEM tools can generate compliance reports, track user activities, and provide evidence of security controls, thereby supporting organizations in demonstrating adherence to industry standards and regulations.
Some popular SIEM tools include:
4.4.1 Splunk
Splunk is a powerful platform used for monitoring, searching, analyzing, and visualizing machine-generated data. It collects and indexes data from various sources, including logs, events, and metrics, and provides real-time insights and actionable intelligence. Splunk’s features include powerful search capabilities, data visualization, alerting, and machine learning. It helps organizations gain valuable insights from their data and enables effective troubleshooting, security monitoring, and business intelligence.
4.4.2 ELK Stack (Elasticsearch, Logstash, Kibana)
The ELK Stack, now known as the Elastic Stack, is a combination of three open-source tools:
Elasticsearch: Elasticsearch is a highly scalable and distributed search and analytics engine. It stores and indexes data in near real-time, allowing for fast and efficient search, analysis, and retrieval of structured and unstructured data.
Logstash: Logstash is a data collection and processing pipeline. It helps in ingesting and parsing data from various sources, such as logs, metrics, and event streams. Logstash enables data transformation and enrichment before sending it to Elasticsearch for indexing and analysis.
Kibana: Kibana is a data visualization and exploration tool that works in conjunction with Elasticsearch. It provides a web-based interface for querying and visualizing data stored in Elasticsearch. Kibana offers powerful visualization options, dashboards, and search capabilities, enabling users to interactively explore and gain insights from their data.
4.4.3 IBM QRadar
IBM QRadar is a security information and event management (SIEM) platform that helps organizations detect and respond to security threats. It collects and correlates log data from various sources, including network devices, servers, and applications, to provide comprehensive visibility into security events. QRadar offers features like real-time threat detection, incident response workflows, log analysis, and security event correlation. It utilizes advanced analytics and machine learning algorithms to identify potential security incidents and provides actionable insights to security analysts.
IBM QRadar is widely used for security monitoring, threat detection, and compliance reporting, helping organizations proactively identify and mitigate security risks.
5. Open-Source Tools and Projects
| Tool/Project Name | Key Features | Primary Use Case |
|---|---|---|
| Jenkins | Extensive plugin ecosystem, distributed builds easy integration with version control systems. | Building, testing, and deploying applications in a continuous integration and delivery pipeline. |
| Ansible | Agentless architecture, declarative language, and a large community-driven library of modules. | Configuration management, application deployment, and infrastructure orchestration. |
| Docker | Containerization, portability, and efficient resource utilization. | Application deployment, microservices architecture, container orchestration. |
| Kubernetes | Scalability, high availability, self-healing capabilities, and service discovery. | Container orchestration, managing complex microservices architectures. |
| Git | Branching, merging, version history, collaboration. | Source code management and collaboration among developers. |
| Prometheus | Time-series database, flexible query language, extensive integrations. | Monitoring infrastructure, applications, and services. |
| Grafana | Customizable dashboards, a wide range of data source integrations, and alerting capabilities. | Monitoring, observability, and visualization of metrics and logs. |
| Terraform | Declarative language, multi-cloud support, dependency management. | Infrastructure provisioning and management in a cloud environment. |
| Nagios | Monitoring host and service availability, alerting, and extensibility through plugins. | Monitoring and alerting for infrastructure and applications. |
| Gradle | Dependency management, multi-project builds, extensible plugin system. | Building and packaging software projects. |
6. Resources for learning DevSecOps
Here are some resources for learning DevSecOps.
- What is DevSecOps? – Red Hat
- DevSecOps on AWS – Amazon Web Services
- Introduction to DevSecOps – IBM Cloud