Cloud Native Applications with JWT
A native cloud application is an application that is developed for a cloud computing environment.
There is no specific answer to the question ” what is a cloud-native application” but different concepts that must be met.
One of the most important in my opinion is the ability to scale up and down at a rapid rate. And this means that our applications cannot have any state on each of the servers since if one server goes down or is scaled down, then the state stored in that server will be lost.
This is very well summarized at https://www.youtube.com/watch?v=osz-MT3AxqA where it is explained with a shopping cart example. In monolith approach, you store the products of the shopping cart in a server session, if the server went down then all products of shopping cart were lost as well. In a cloud-native app, where server instances can be scaled up and down quickly, it is important to not have this stateful behavior on your services and design them to be stateless.
There are different approaches to achieve this goal of implementing a stateless architecture but they can be summarized into two categories:
- Use a distributed in-memory key/value data store like Infinispan.
- Use a token which acts as a session between client and server using for example JWT.
In this post, I am going to introduce you the later approach.
From https://jwt.io/introduction/ site:
JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object.
This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret using HMAC or a public/private key pair using RSA.
JSON Web Tokens consist of three Base64Url strings separated by dots which are: Header.Payload.Signature
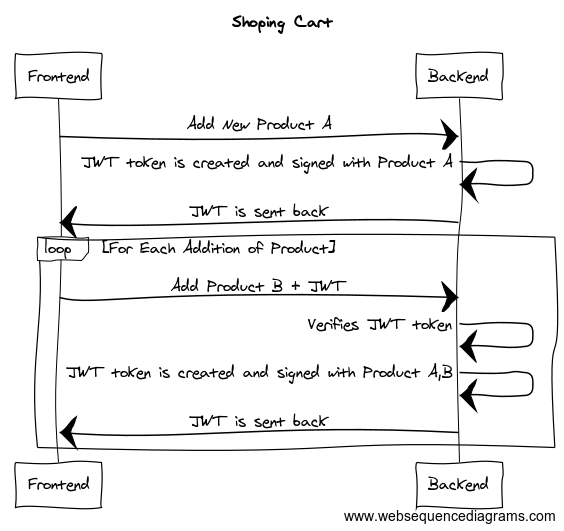
So the idea basic idea for implementing stateless architecture on backend using JWT is the next one:
- When the user adds the first product, the backend service generates a new JWT token with the product added and sent it back to the frontend.
- When the user adds a new product, it sends the product to add and also the JWT token that was sent before by backend.
- Then the backend verifies that the token has not been modified (verifying the signature), then it gets the products from JWT payload added previously and add the new one to the list. Finally, it creates a new token with previous and new products and it sent it back to the frontend.
- The same process is repeated all the time.
So as you can see, now it is not necessary to maintain any state or add any new database service on backend side, you just need to sent back and forward the JWT token with the products inside.
I have recorded a video of a simple shopping cart example where I show the stateless nature of the solution. It can be seen at:
Also if you want to check the project that I used for recording you can take a look at https://github.com/lordofthejars/shop-jwt.
Notice that this is just a simple post so you can get the basic idea. But you need to take into consideration next things to use it in production:
- Use HTTPS instead of HTTP
- JWT just signs the token, if you want extra protection apart from HTTPS, use JWE to encrypt the payload of JWT token as well.
- Fingerprinting the token to avoid any man-in-the-middle attack and use these parameters as authentication parameters for the token.
- JWT can be used for passing authentication and authorization things as well.
You can watch my talk at JavaZone where I introduce some of these techniques:
Make your REST services attack proof – Alex Soto Bueno from JavaZone on Vimeo.
The good part of JWT approach is that it simplifies a lot the deployment of the service, you don’t need to deploy or configure any other distributed database to share the content across the cluster, which minimizes the problems related to the network for communicating to the distributed database or misconfiguring of any of the nodes.
The drawback is that the client needs to be aware to receive and sent back the token and deal with it. In backend side, you need to sign and verify every token all the time.
| Published on Java Code Geeks with permission by Alex Soto, partner at our JCG program. See the original article here: Cloud Native Applications with JWT Opinions expressed by Java Code Geeks contributors are their own. |